| Directories and Files |
|
Permissions |
 |
Web_store |
|
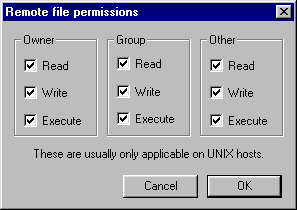
drwxr-xr-x |
|
755 |
| |
 |
ws400CS.cgi |
|
-rwxr-xr-x |
|
755 |
| |
 |
ws_banner.cgi |
|
-rwxr-xr-x |
|
755 |
| |
 |
ws_delete_files.cgi |
|
-rwxr-xr-x |
|
755 |
| |
 |
ws_delete_files.cron |
|
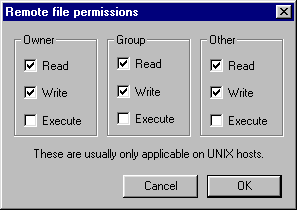
-rw-r--r-- |
|
644 |
| |
 |
ws_editor.cgi |
|
-rwxr-xr-x |
|
755 |
| |
 |
ws_global.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
ws_mail.cgi |
|
-rwxr-xr-x |
|
755 |
| |
 |
Databases |
|
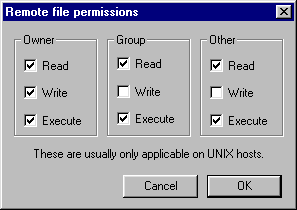
drwxrwxrwx |
|
777 |
| |
 |
Access.Client.Password.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Access.Client.Phone.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Access.Restrict.Password.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Access.Restrict.Phone.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Client.Retrieve.Password.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Client.Retrieve.Phone.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Demo.OrderForm.AuthorizeNet.CreditCard.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Demo.OrderForm.CreditFaxMail.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Demo.OrderForm.Surepay.Check.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Demo.OrderForm.Surepay.CreditCard.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Form.Catalog.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Form.Reseller.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
No_Frames.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.AuthorizeNet.Check.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.AuthorizeNet.CreditCard.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.Check.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.CreditCard.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.CreditFaxMail.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.FaxMail.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.Surepay.Check.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
OrderForm.Surepay.CreditCard.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
outlet.data |
|
-rw-rw-rw- |
|
666 |
| |
 |
outlet.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
outlet.state_country.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
outlet_editor.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Pre.OrderForm.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Resellers.data |
|
-rw-rw-rw- |
|
666 |
| |
 |
Resellers.data.readonly | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Resellers.data.txt_editor.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
Resellers.data_editor.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
ws_banner.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
ws_mail.setup |
|
-rw-r--r-- |
|
644 |
| |
 |
ws_userfile.users | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Clients |
|
drwxrwxrwx |
|
777 |
| |
 |
.client files | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Restricted |
|
drwxrwxrwx |
|
777 |
| |
 |
.client files | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Mail |
|
drwxrwxrwx |
|
777 |
| |
 |
MSG.1998-11-01.08-28-46_PM.FAQ.list |
|
-rw-rw-rw- |
|
666 |
| |
 |
WebStore.list | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Sales | WebStore Generated |
|
drwxrwxrwx |
|
777 |
| |
 |
delete.short-term.age.file | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
2xxx (4 digit current year) | WebStore Generated |
|
drwxrwxrwx |
|
777 |
| |
 |
.acs files | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
.txt files | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Docs |
|
drwxr-xr-x |
|
755 |
| |
 |
HTML Support Documents |
|
-rw-r--r-- |
|
644 |
| |
 |
Images |
|
drwxr-xr-x |
|
755 |
| |
 |
HTML Support Document Images |
|
-rw-r--r-- |
|
644 |
| |
 |
Graphics |
|
drwxr-xr-x |
|
755 |
| |
 |
WebStore Image Files |
|
-rw-r--r-- |
|
644 |
| |
 |
Banners |
|
drwxr-xr-x |
|
755 |
| |
 |
WS Banner Image Files |
|
-rw-r--r-- |
|
644 |
| |
 |
Html |
|
drwxr-xr-x |
|
755 |
| |
 |
WebStore HTML Files |
|
-rw-r--r-- |
|
644 |
| |
 |
Library |
|
drwxr-xr-x |
|
755 |
| |
 |
WebStore Program Libraries |
|
-rw-r--r-- |
|
644 |
| |
 |
Real-time Merchant Configuration Files |
|
-rw-r--r-- |
|
644 |
| |
 |
Logs |
|
drwxrwxrwx |
|
777 |
| |
 |
AuthorizeNet.log | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Surepay.log | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Whois.log | WS Mail Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Pgp |
|
drwxr-xr-x |
|
755 |
| |
 |
config.txt |
|
-rw-r--r-- |
|
644 |
| |
 |
pubring.pgp | Server Created |
|
-rw-r--r-- |
|
644 |
| |
 |
randseed.bin | Server Created |
|
-rw-r--r-- |
|
644 |
| |
 |
Statistics |
|
drwxrwxrwx |
|
777 |
| |
 |
WebStore_Access.counter | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WebStore_Access.stats | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WebStore_Query.stats | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WSEditor_Access.stats | WS Editor Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WSEditor_Query.stats | WS Editor Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WSMail_Access.stats | WS Mail Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
WSMail_Query.stats | WS Mail Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
User_carts |
|
drwxrwxrwx |
|
777 |
| |
 |
990328065106341.bnr | WS Banner Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
990328065106341.cart | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
cron.age.file | WS Delete Files Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
cron.file.counter | WS Delete Files Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
delete.banner.age.file | WS Banner Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
delete.cart.age.file | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Restricted |
|
drwxrwxrwx |
|
777 |
| |
 |
990328065106355.cart | WebStore Generated |
|
-rw-rw-rw- |
|
666 |
| |
 |
Users |
|
drwxrwxrwx |
|
777 |
| |
 |
990328065106341.usr | WS Editor & WS Mail Generated |
|
-rw-rw-rw- |
|
666 |